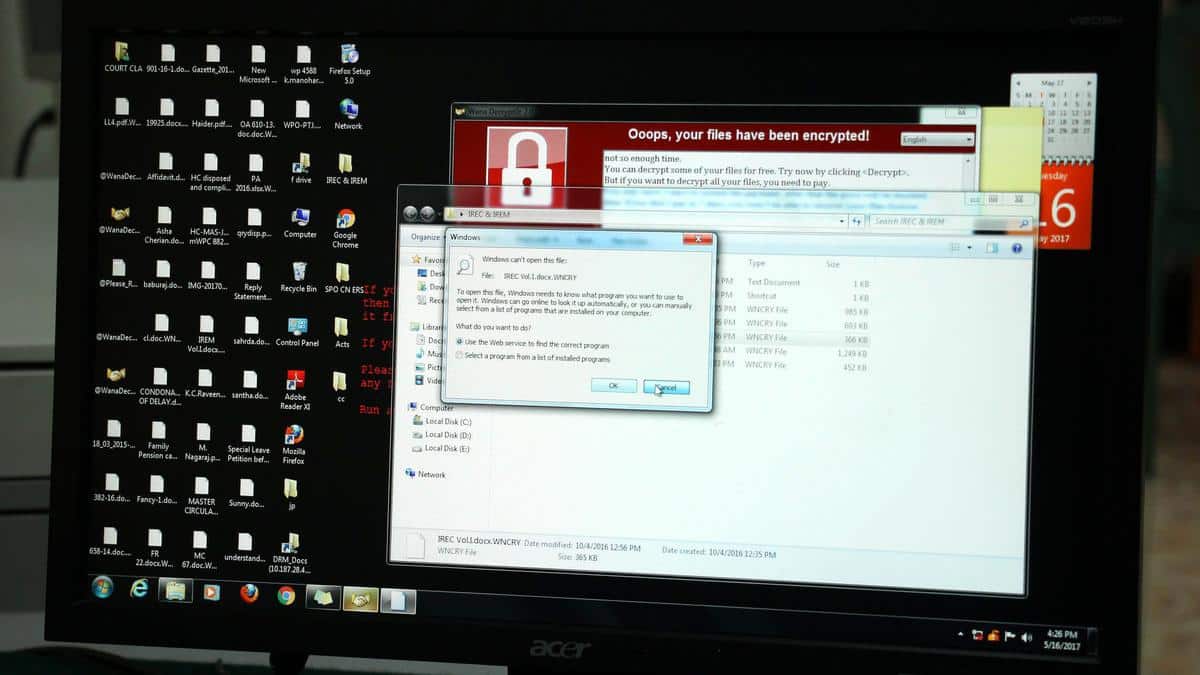
About Akira Ransomware:
- It is designed to encrypt data, create a ransomware note and delete Windows Shadow Volume copies on affected devices.
- The ransomware gets its name due to its ability to modify filenames of all encrypted files by appending them with the “.akira” extension.
How does Akira Ransomware work?
- The ransomware is designed to close processes or shut down Windows services that may keep it from encrypting files on the affected system.
- It uses VPN services, especially when users have not enabled two-factor authentication, to trick users into downloading malicious files.
- The ransomware also terminates active Windows services using the Windows Restart Manager API, preventing any interference with the encryption process.
- It is designed to not encrypt Program Data, Recycle Bin, Boot, System Volume information, and other folders instrumental in system stability.
- It also avoids modifying Windows system files with extensions like .syn. .msl and .exe.
- Once sensitive data is stolen and encrypted, the ransomware leaves behind a note named akira_readme.txt which includes information about the attack and the link to Akira’s leak and negotiation site.
- Each victim is given a unique negotiation password to be entered into the threat actor’s Tor site.
- Unlike other ransomware operations, this negotiation site just includes a chat system that the victim can use to communicate with the ransomware gang.
How does ransomware infect devices?
- Ransomware is typically spread through spear phishing emails that contain malicious attachments in the form of archived content (zip/rar) files.
- Other methods used to infect devices include drive-by-download, a cyber-attack that unintentionally downloads malicious code onto a device, and specially crafted web links in emails, clicking on which downloads malicious code.
- The ransomware reportedly also spreads through insecure Remote Desktop connections.
Q1) What is An operating system?
An operating system (OS) is a software program that manages computer hardware and software resources and provides services for computer programs. It acts as an intermediary between applications and the computer hardware, allowing users and applications to interact with the computer efficiently and effectively.
Source: What is the Akira ransomware, and why has the government issued a warning against it?
Last updated on February, 2026
→ UPSC Notification 2026 is now out on the official website at upsconline.nic.in.
→ UPSC IFoS Notification 2026 is now out on the official website at upsconline.nic.in.
→ UPSC Calendar 2026 has been released.
→ Check out the latest UPSC Syllabus 2026 here.
→ Join Vajiram & Ravi’s Interview Guidance Programme for expert help to crack your final UPSC stage.
→ UPSC Mains Result 2025 is now out.
→ UPSC Prelims 2026 will be conducted on 24th May, 2026 & UPSC Mains 2026 will be conducted on 21st August 2026.
→ The UPSC Selection Process is of 3 stages-Prelims, Mains and Interview.
→ Prepare effectively with Vajiram & Ravi’s UPSC Prelims Test Series 2026 featuring full-length mock tests, detailed solutions, and performance analysis.
→ Enroll in Vajiram & Ravi’s UPSC Mains Test Series 2026 for structured answer writing practice, expert evaluation, and exam-oriented feedback.
→ Join Vajiram & Ravi’s Best UPSC Mentorship Program for personalized guidance, strategy planning, and one-to-one support from experienced mentors.
→ UPSC Result 2024 is released with latest UPSC Marksheet 2024. Check Now!
→ UPSC Toppers List 2024 is released now. Shakti Dubey is UPSC AIR 1 2024 Topper.
→ Also check Best UPSC Coaching in India