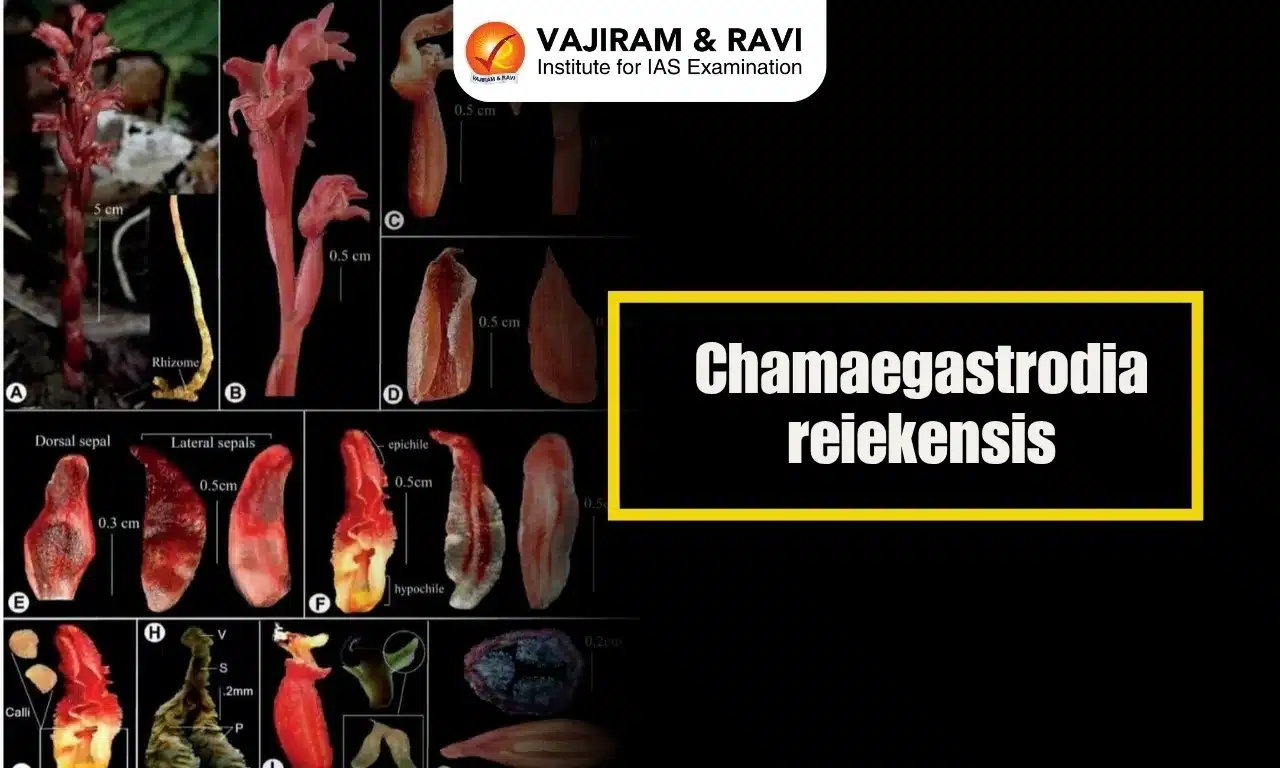
About End-to-end encryption (E2EE)
- Encryption is a way of protecting data from unauthorised access or tampering.
- It works by transforming the data into a secret code that only the intended recipient can decipher. This comes in useful for various cases, such as securing online communications, storing sensitive information, and verifying digital identities.
- There are two main types of encryption:
- Symmetric: It uses the same key to encrypt and decrypt the data. In symmetric encryption, the key used to encrypt some information is also the key required to decrypt it.
- Asymmetric: It uses a pair of keys: one public and one private. The public key can be shared with anyone, but the private key must be kept secret.
- The term encryption is generally used when referring to the privacy of stored data, while end-to-end encryption protects data as it’s transferred between a location – which is crucial wherever there’s a rapid exchange of information.
- In an E2EE-enabled app, only the person on each end – the sender and receiver – can read any exchanged messages.
- This is because messages get encrypted on your device before being sent and only are decrypted when they reach your intended recipient.
Issues with End-to-end encryption
- Some potent malware can also ‘snoop’ on your messages by infiltrating your device via other means – an SMS and reading them before they are encrypted.
- The company that installs E2E encryption on its products can install a backdoor or an exception that allows the company to surmount the encryption and access the messages.
Q1) What is the Chameleon Trojan?
It is a malware that has the ability to disable biometric authentication methods, including fingerprint and face unlock, to sneakily access sensitive information.
Source: What is end-to-end encryption? How does it secure information?
Last updated on July, 2025
→ UPSC Notification 2025 was released on 22nd January 2025.
→ UPSC Prelims Result 2025 is out now for the CSE held on 25 May 2025.
→ UPSC Prelims Question Paper 2025 and Unofficial Prelims Answer Key 2025 are available now.
→ UPSC Calendar 2026 is released on 15th May, 2025.
→ The UPSC Vacancy 2025 were released 1129, out of which 979 were for UPSC CSE and remaining 150 are for UPSC IFoS.
→ UPSC Mains 2025 will be conducted on 22nd August 2025.
→ UPSC Prelims 2026 will be conducted on 24th May, 2026 & UPSC Mains 2026 will be conducted on 21st August 2026.
→ The UPSC Selection Process is of 3 stages-Prelims, Mains and Interview.
→ UPSC Result 2024 is released with latest UPSC Marksheet 2024. Check Now!
→ UPSC Toppers List 2024 is released now. Shakti Dubey is UPSC AIR 1 2024 Topper.
→ Also check Best IAS Coaching in Delhi